DDoS | Distributed Denial Of Service Attack
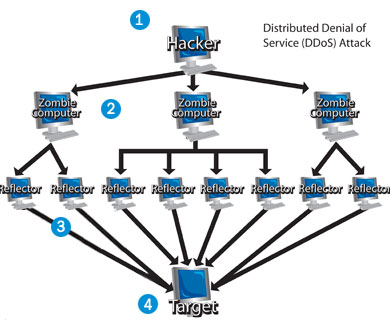
Distributed Denial Of Service (DDoS) Attack is large scale DoS attack conducted with help of zombie systems or botnets on vulnerable target systems. Indirectly we can say a DDoS is launched via huge network of compromised systems. DDoS attack uses many computers to launch a coordinated DoS attack against one or more target.
Using client/server technology (same as we do it in RAT clients), the attacker is able to multiply the effectiveness of the denial of service significantly by harnessing the resources of multiple computers to serve for attack. In most of the cases the zombie system user never come to know about his/her system is performing a DoS attack since an attacker can put condition to be low on bandwidth usage per zombie.
Using client/server technology (same as we do it in RAT clients), the attacker is able to multiply the effectiveness of the denial of service significantly by harnessing the resources of multiple computers to serve for attack. In most of the cases the zombie system user never come to know about his/her system is performing a DoS attack since an attacker can put condition to be low on bandwidth usage per zombie.
The victims compromised for performing an attack are known as “secondary victim” where as the target on whom attack will be performed is known as “primary victim”. An attacker generally gains administrative privilege on secondary targets to launch attack on primary target. Once attacker gains administrative privilege on secondary victim, he/she uploads DDoS program or script to launch an attack on primary victim. If an attacker has network of 30000 plus zombies then launched attack is nearly impossible to counter because number of IP address is too much for a single server to handle per second. DDoS are dangerous because they can even pull down very big hosts like yahoo and bing to their feet.
Most organizations secure themselves with a firewall but a firewall does not really guarantee against DDoS. A very good but badly administrated firewall can even lead to fall down of service. Conducting a DDoS attack is much simple than it appears if you already have thousands of compromised system. In fact in most cases you don't even need already created tools you can manually create your own tools if you have little programming knowledge of C and C++ and little about windows and Linux commands. In future posts I ll show you how you can create your own script to launch a DDoS attack.
Following are steps involved in conducting DDoS attack:
1.Compromise thousands of systems using RAT clients or botnets.
2.Write a program or script that can conduct attack
3.Trigger Zombies for attack
4.Don't stop until the target is down.
Dear visitors I am covering basics of Denial Of Service Attacks because in coming posts I ll be covering different ways to launch DoS attacks. You are requested to read and grasp every basic detail before I show you real attacking methodologies. Thanks for reading and keep visiting.